5 Authentication Models That Give Us A Glimpse of the Future

When talking about security and protection of individual identities and company data, we chief executives should always consider the future. What does this mean? While we manage present problems, we also need to speculate about threats and possibilities. We have to prepare against potential attacks to our system, which will compromise confidential information and cost our business dearly.
In this light, I am presenting to you these five methods that can be integrated into your identity and access management (IAM):
Single sign-on
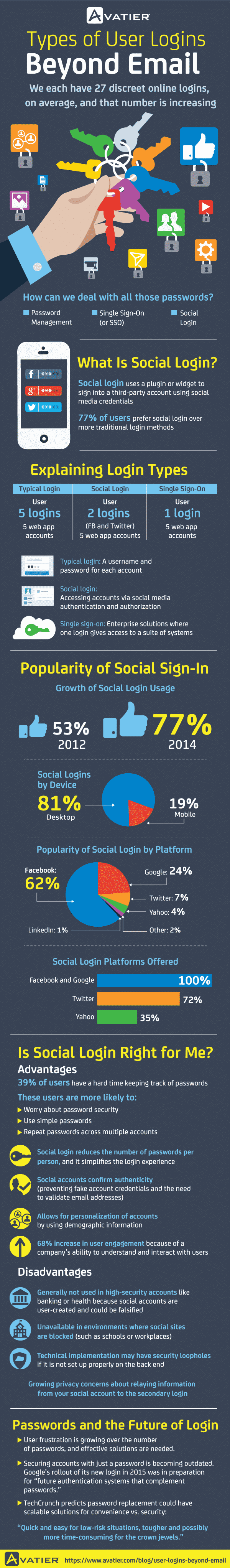
The average digital consumer keeps around 27 accounts on various apps and sites. To craft medium to strong passwords for each of them, you need at least 12 characters combining letters, numbers, and symbols. I only remember three out of the six sets of credentials I use for major logins. Since my responsibility grew, other pieces of information have taken up space in my head. My kind of approach won’t cut it in the future, in which people will be relying more on mobile devices.
I find the single sign-on (SSO) model helpful in lightening the mental work without compromising security. With SSO, you need a master password to access several accounts. The most popular example today is social login. About 77% of users prefer it, according to IAM expert Avatier. Through plugins and widgets, the likes of Facebook and Twitter allow you to use your social media credentials to sign into their partner apps and websites.
While one can argue that we should scrap passwords altogether, a single portal that requires one set of login credentials can help employees enter a system and switch from one tool to another seamlessly. Check out the following infographic to further understand how SSO works.
Fingerprint sensor
We already see common applications of touch sensors, from our homes to smartphones. Apple and Samsung have been deploying their own fingerprint recognition tech on their devices. Native touch identification is still limited to unlocking your phone. But there are apps that let you use the same approach, so you can add a layer of security to accounts that contain personal or sensitive information.
As with other biometric authentication models, you are the password here. It will be tougher for attackers to break in. But touch ID also needs to be a part of a multi-factor system, given that gadgets can be lost or stolen.
Iris scan
The eye is another sophisticated body part that plays a role in IAM. It is said to be 10 times more accurate than fingerprints. More specifically, though, your iris holds the key — not the retina. The iris is the colored portion surrounding the pupil. You may describe yourself as blue-eyed or brown-eyed. But in reality, your irises are not just about the pigments. They are more complex than they look. Each set is uniquely yours, too.
To date, iris scans are used in more advanced facilities. One of the challenges in bringing it into the mainstream is its high upfront costs. For this reason, it is also largely untested. Plus, there are security concerns that can arise from the tech: criminals creating a high-def copycat of irises or even gouging out eyeballs. Still, I’m positive that iris scans will develop into a more reliable authentication method.
Voice recognition
Speaker recognition is another option from the biometrics list. It is simpler and easier to use because, well, it is natural for humans to speak. No special hardware is needed as it mostly comes built-in with the phone. Voice scans have one advantage over iris and fingerprint scans: they facilitate remote authentication. Users do not need to hold their phone to activate it.
However, voice print can change over time. But identifying and verifying users through voice patterns is leading somewhere, given the amount of research and development giant companies like Google put into it.
Adaptive authentication
This approach detects and assesses changes in user behavior. It relies on factors such as the speed by which the users typed in their password or the way they moved their mouse. When something does not compute, a fedscoop interview with SecureAuth and Defense Advanced Research Projects Agency says “it can automatically force them through additional security steps and alert the security team.” Adaptive authentication is very promising in that it analyzes behavioral cues to detect a breach from the baseline (password login) down to the subsequent layers of security.
Have you read?
For more inspiration and information regarding the role of CEOs in company security, read Digital Security Starts In the C-Suite by Karl Zimmerman.
How CEOs can plan for the long-term by Vikas Agrawal.
Add CEOWORLD magazine to your Google News feed.
Follow CEOWORLD magazine headlines on: Google News, LinkedIn, Twitter, and Facebook.
This report/news/ranking/statistics has been prepared only for general guidance on matters of interest and does not constitute professional advice. You should not act upon the information contained in this publication without obtaining specific professional advice. No representation or warranty (express or implied) is given as to the accuracy or completeness of the information contained in this publication, and, to the extent permitted by law, CEOWORLD magazine does not accept or assume any liability, responsibility or duty of care for any consequences of you or anyone else acting, or refraining to act, in reliance on the information contained in this publication or for any decision based on it.
Copyright 2024 The CEOWORLD magazine. All rights reserved. This material (and any extract from it) must not be copied, redistributed or placed on any website, without CEOWORLD magazine' prior written consent. For media queries, please contact: info@ceoworld.biz
SUBSCRIBE NEWSLETTER