What is the optimal technology stack for Operational Technology Cybersecurity: Learnings from an IBM OT Security Leader

Learnings from a senior OT security leader at IBM on the technology stack most suited for building comprehensive operational security programs across critical infrastructure industries
Operational technology (OT) refers to industrial control systems that are used to perform automation tasks such as Programmable Logic Controllers (PLCs) and Remote Terminal Units (RTUs). These are in turn overseen by Supervisory Control and Data Acquisition (SCADA) systems and Distributed Control Systems (DCS). These devices form the core of plant automation where activities can be largely automated with minimal human intervention, such as obtaining pressure readings from valves, performing line inspections and so on. OT systems are ubiquitous across all critical infrastructure industries such as Power, Oil and Gas, Automotive, Water Utilities and Transportation. OT infrastructure is very vital to any nation’s security for ensuring delivery of essential services to their citizens, more so than regular IT infrastructure. The ever-increasing cyberattacks on critical infrastructure such as the ransomware on a semiconductor manufacturer in Taiwan, Colonial Pipeline attack in the US and the cyber-attack on Ukraine’s power grid causing outages can result massive disruptions to operations in addition to financial and reputational loss. Given the absolute criticality of this domain, OT cybersecurity is getting the highest priority from all nations such as creation of National Cybersecurity Strategy in US, the CHIPS act, and EU cybersecurity act.
In this article, we discuss with Krishna Tata, an OT cybersecurity leader from the US, on what is the primary and most effective technology stack for securing the OT infrastructure for organizations. Krishna is a thought leader and inventor in OT security, who has built several products for the IBM security products portfolio including award winning ones such as IBM QRADAR SIEM and SOAR and has built their OT security practice. He has also built one of the largest teams of OT security professionals in the world at IBM. Krishna has been engaged in cutting-edge OT cybersecurity product development and research at IBM and has been helping critical infrastructure clients since 2015 in addressing critical security issues.
We leverage his expertise to discuss the various strategies available to organizations in terms of the technology stack available and technical controls that can be implemented to secure OT networks from cyber-attacks.
What are the unique characteristics of the OT networks, and how are they different from IT networks?
“Critical Infrastructure is often used as an umbrella term to describe control devices within Operational Technology (OT) networks, which are used for process automation. They are generally Programmable Logic Controllers (PLCs) or remote terminal units (RTUs). Both are integral in OT networks to perform operations around process control automation, which could include things such as monitoring the pressure of a valve, controlling the speed of a rotor or the direction of a production line. Distributed Control Systems (DCS) control entire facilities and have a single bus with branches connected by controllers and other devices, that stretch across a vast geographical area. A layer of supervisory control on top of the PLCs aggregates all this data into a Supervisory Control and Data Acquisition System (SCADA).”
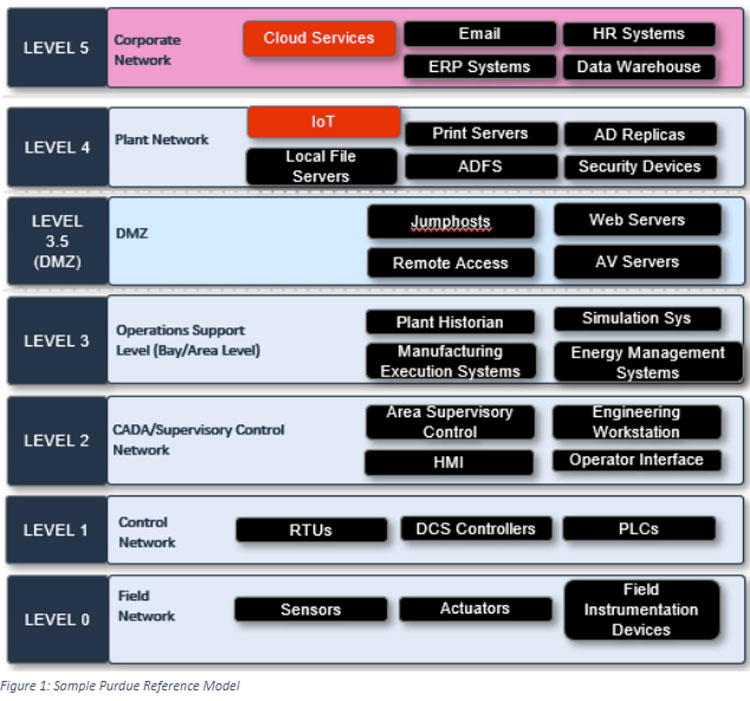
“The Purdue enterprise reference model has been used as a de facto automation architecture model for decades now for industrial automation. divides networks into logical swimlanes, with each swimlane having a certain family or type of devices. Level 0 refers to field devices such as sensors, actuators, valves, while level 1 has the OT automation devices such as PLCs, level 2 has SCADA systems and DCS systems, while levels higher than that go into the overall plant network and the corporate network. While this model served well in an era when ‘smart’ or ‘connected’ didn’t mean much, the reality today is vastly different. Connected devices don’t straddle these swimlanes, can communicate wirelessly to aggregators from anywhere, have access to internet and run protocols that are not always encrypted. So, OT infrastructure in reality is vastly more complex than IT infrastructure” explains Krishna.
What are the major cyber threats facing operational technology and how to they differ from conventional IT?
“Cyber threats to operational technology follow vectors, also called attack patterns, that are vastly different from that of conventional attacks on information technology infrastructure. I see them in five broad categories (a) Identity and access management vectors, (b) Network security vectors, (c) Malware in OT networks, (d) OT device vulnerabilities and (e) security profiles. For example, access to program or control PLCs are generally restricted to site engineers or operators, as improper access to a PLC could result in the PLC being reprogrammed in order to carry out malicious tasks such as closing of safety valves. Network security vectors include things such as abnormal communication patterns between a PLC and an engineering workstation. A compromised engineering workstation could have programs that are meant to control PLCs and result in abnormal traffic signatures traversing the entire network because of insufficient network controls. Lack of network segmentation and micro-segmentation in OT networks and prevalence of flat networks results in abnormalities easily spreading across plants and causing shutdowns. This is the same thing that allows malware such as Log4j and Stuxnet to spread easily in OT networks, because security checks and controls are lacking.”
Also, we need to keep in mind that a lot of these devices were never really built with security in mind. PLCs, for example, were just meant to do repetitive automation tasks and no one could ever imagine back in the 60s and 70s that these devices could be hacked. Now that these devices are connected to internet-of-things (IoT) sensors, have presence of newer technologies such as 5G and often also access to internet, the threats have also grown exponentially. Now, suddenly security needs to be factored into these devices, which are legacy in many cases and are also extremely sensitive to any changes” Krishna elaborates.
What is the right technology infrastructure that organizations require to implement to protect their OT networks?
“Just as in other critical domains such as information technology, cloud or data lakes, security for OT infrastructure has also evolved over the past decade to decade and a half. We have a host of technologies that have been purpose built to serve cybersecurity for operational technology infrastructure. Some of them are:
- Industrial Intrusion Detection Systems (IIDS): These tools are often ruggedized devices that sit inside industrial control networks and can passively sniff the traffic within control networks over the wire. They are very powerful tools used to analyze abnormal traffic patterns such as SMB ping storms or high amounts of TCP reconnects, which can point to either configuration errors or worse malware within networks. These tools make use of signature-based algorithms such as YARA rules, SNORT and STIX rules to identify key network signatures that are indicative of abnormal behavior. Anomalous behavior could also include persistent malware such as Log4j, Stuxnet or other malware that can wreak havoc in these environments. In addition, they also have artificial intelligence (AI) based behavioral learning modules that can detect seemingly innocuous alerts which when put together can indicate compromising patterns in totality. For example, the registry key values on an engineering workstation could have changed, resulting in multiple TCP SYN requests being sent to a PLC and finally establishing connection with a PLC. In isolation, they might appear benign, but using AI-based heuristics, these tools can tell you the full story of the attack vector. Companies such as Nozomi Networks, Claroty, Darktrace, Armis and Microsoft are leaders in this segment, each having a powerful suite of products to enable detection.
- Industrial Identity and Access Management Solutions: These tools are meant to address the critical aspect of role-based access control for devices within the industrial control systems. They effectively act as gatekeepers, very akin to jumpboxes, to obtain access to industrial endpoints such as PLCs or Human machine interfaces (HMIs). If a plant operator or engineer wants to access a PLC to be able to do either routine maintenance tasks or tasks related to gathering telemetry data, they will need to go through one of these tools. They have the capability of logging the actions the end-users perform on each device, restrict access to only devices they are allowed based on their user groups and maintain an audit-trail of configuration changes made on each of these devices. They are powerful enforcers of remote access management and also privileged access management, ensuring that critical OT devices are accessible only to users with a valid need-to-know based on their organizational roles and groups.
- OT Firewalls: These tools work in combination with industrial intrusion detection systems and identity and access management systems to enforcement blocking of certain types of communications and traffic based on pre-determined rules. They differ from conventional firewalls in their support of industrial specific protocols such as Modbus, Profinet and so on. Based on architectural rules, ports and protocols based on the rules that are configured in these firewalls they can block ingress of egress traffic flowing through them to enforce isolation of networks and also ensuring any potential malware or undesirable connections don’t materialize.
- Network Access Control (NAC) solutions: These solutions are meant to enforce network segmentation within OT networks. Cisco ISE is a great example of one such solution. It gives the capability to micro-manage the communication between subnets and zones of particular types of devices with one another. For example, if there are Yokogawa controllers in a particular subnet and they have no business reason to be communicating with HMIs in a different subnet, this can be enforced at a granular level using NAC solutions, where devices are blocked from joining certain networks based on specific variables. They are also referred to as device access control solutions and can be enforced even at an individual device level to enforce zero-trust micro-segmentation.
- Uni-directional Gateways: Also referred to as data diodes, these are powerful technologies used in OT netwotks for network isolation. They have the capability to enforce uni-directional flow of traffic at a hardware level. In this they differ from firewalls, where firewalls enforce it at a logical level or in the control plane, where uni-directional gateways make it physically impossible for traffic to pass in a particular direction. For example, say a rail signaling system needs to make it’s database available outside of the control network for the scheduling teams to look at it and make real-time railway scheduling possible. They can use uni-directional gateways in this case as it will allow traffic only one-way, i.e., from the control networks to the corporate network and never vive-versa. Companies such as Waterfall and Owl have market leading products and are prime examples of this.
- Security Incident and Event Management (SIEM) tools: These tools act as the single pane of glass for all security alerts coming from a myriad of sources. This is the tool that security analysts will look into to identify possible ‘offenses’ or security events that need to be actioned upon. SIEM tools leverage powerful APIs to integrate with other security tools in order to obtain the security alerts that need to mitigated or remediated. They have powerful in-built artificial intelligence modules that can auto-resolve false positives and only pass alerts that are considered valid or genuine. This drastically cuts down the time it takes analysts to sift through various tools to identify alerts and act on each one of them, whether they are valid alerts or not. IBM QRADAR SIEM, Splunk Security Enterprise and HP ArcSight are some of the leading examples of such technologies.
- Security Orchestration, Automation and Response Solutions: These technologies are a new innovation within the OT security industry. They’ve made the previously unthinkable aspect of automated response within OT networks a reality by allowing for auto-resolution of alerts within OT networks. OT networks have been traditionally extremely averse to any sort of automated actions that can touch the OT endpoints such as PLCs or RTUs, given the high premium placed on availability. However, with SOAR technologies it is possible now to safely take actions within the realm of risk tolerance of an organization that mitigate risks and security alerts, such as turning off SMB v1.0 on certain Windows based HMIs.
Of course, the entire list of possible technologies that can be implemented to secure OT networks is quite exhaustive, but these are the major ones” summarizes Krishna.
Key Pillars of a Successful OT Cybersecurity Programs
“As mentioned earlier, though the technology stack is vital and integral, they cannot function without a holistic end-to-end cybersecurity program. This includes, of course, security hygiene which is even more critical in OT environments than in others. Assuming that the reader has some level of familiarity with operational technology (OT) and cybersecurity, these are two high-level principles that are critical for success when implementing an OT cybersecurity program:
- Understand the nuances of OT Environment and Architecture
Every OT network has its own origin story and its own vendor makeup. Understanding the vendors, their proprietary protocols, the controls needed, and their architectures is essential. This ensures risks are properly assessed and controls designed accordingly. A deep understanding of the overall architecture, system components, how they interact with each other, what protocols they use and what vulnerabilities exist in them is critical. Additionally, it’s important to have visibility of any legacy systems, end-of-life systems and how they might interface with new OT technologies. - Create an OT security reference architecture
A clear OT cybersecurity reference architecture with the illustration of major domains or capabilities such as Network Security, Device Security, Identify and Access Management, Data Security, Security Hygiene and so on imperative to a successful program. Executive leadership’s involvement in laying out the framework or reference architecture and defining the end-to-end program to achieve the goals of each of these capabilities is very vital. - Define Clear Roles and Responsibilities for OT Cybersecurity
Security monitoring and operations is a 24×7 job, just like in the armed forces. As the saying goes, you snooze you lose. It’s imperative that there is a clear understanding of who owns what and who’s responsible for specific tasks. Therefore, someone should be assigned as the OT cybersecurity program owner (or champion), given the responsibility for defining roles/responsibilities and overseeing the program. Other critical roles include:OT cybersecurity teams: These teams should have an intimate knowledge of the OT environment and architecture in order to properly assess risks, develop controls, and support incident response. This can either be a dedicated OT security team or security staff that works within an industrial automation group or control systems group.
IT security teams: While IT may not have as much overall visibility into OT assets as OT/controls staff or cybersecurity teams (due to segmentation between IT and OT networks), they still need to be involved in policies/procedures, system updates/patches, access controls, etc. It’s essential that both IT and OT departments work together so that security improvements wrap around both environments adequately.
Executive leadership: Executive leadership support is key to all the concerned parties and teams working together and in the defined strategic direction” summarizes Krishna
The Future of OT Security
“With the newer push to industry 4.0, that leverages sophisticated OT manufacturing processes, more connected Internet of Things (IoT) protocols such as Bluetooth, NFC and so on will continue to grow. Industry 4.0, makes OT security as a primary imperative in an era where increased automation using robotics and generative artificial intelligence is taking shape. Control networks are very curious use cases, as they are relics of the past with PLCs and RTUs dating back decades, in an environment that is increasingly bolting on next-generation technologies such as IoT sensors. Wireless communications and 5G deployments have also become increasingly common. There are many potential benefits of Industry 4.0 and the IoT, but there are also new risks that need to be considered. I do see the industry evolving rapidly with newer tools and technologies coming in to replace ones that are not working efficiently. We are in for exciting times for OT cybersecurity.” concludes Krishna. Coming from one of the foremost leaders in OT cybersecurity, these are prescient words that will need to be kept under close consideration for a safer and more secure world of OT cybersecurity.
Have you read?
The 21st Century’s Biggest Financial Frauds and Controversies.
The World’s Most Valuable Unicorns, 2023.
The World’s Top 10 Highest-Paid Wealth Management Executives.
Highest paid chief executive officers in the United States in 2022.
Highly-Paid Entertainment Chief Executives.
Highest paid health insurance CEOs.
Bring the best of the CEOWORLD magazine's global journalism to audiences in the United States and around the world. - Add CEOWORLD magazine to your Google News feed.
Follow CEOWORLD magazine headlines on: Google News, LinkedIn, Twitter, and Facebook.
Copyright 2025 The CEOWORLD magazine. All rights reserved. This material (and any extract from it) must not be copied, redistributed or placed on any website, without CEOWORLD magazine' prior written consent. For media queries, please contact: info@ceoworld.biz








