Hacked…! If only I knew…

It’s 2:43am when your buzzing [CEO] phone lights up on your night stand. It’s been a good night’s sleep until now; sipping a Mai Tai under a windy palm on a perfect tropical island beach, what could go wrong? “Hello?” Your IT chief apologizes: “Sorry to wake you Boss. But we’ve been hacked. And I can’t get back in.”
Back in the 1940s computer systems were in their infancy, there was no software or fancy algorithms to help encrypt or decipher secret codes. The most notable cryptography device of the day was Germany’s World War II typewriter-style Enigma machine, which could scramble trillions of letter combinations using an electrical current to randomly spin alpha-numeric rotors. It took the combined efforts of allied spies, the capture of an Enigma machine, and the genius of Cambridge mathematician Alan Turning and colleagues’ calculating machine called the Bombe at Bletchley Park UK to crack the system. Countless Hollywood movies tell the tale well. Ok. So “what” you ask?
Well. Seventy years later by 2011 despite the expansive genius of the early crypto-machine era an updated and intensely modernized Enigma was soon upon us. Using the internet, genius software-designers began to perfect a new insidious tool to wreak havoc using infectious malware computer viruses with indelible names like CryptoLocker, ILoveYou, MyDoom, StormWorm and Slammer. Nobody cared. But then disguised and distributed as infected email files, once opened the “phishing” programs quickly infected the host, and locked access to computer files held for ransom. But unlike the Enigma there was no way to crack the code and get your files back. Welcome to ransomware, you’ve been hacked!
But not all criminals are pure evil. For a few hundred dollars you or a CEO/business owner just like you along with thousands of daily other victims could simply make a small payment to one of a hand-full of digital cash vendors at the time like Ukash, Paysafe, or MoneyPak to unlock your passcode key and files. Still, while these cyber-scams raked in millions of dollars, Ukash, Paysafe and MoneyPak were still banking intermediaries, middlemen who charged fees, tracked payments and had local and legal restrictions. Of course, like most thieves cyber thieves don’t like to have their hands tied behind them with easy money on the table.
Enter the rise of the Blockchain, a publicly stamped digital transaction ledger which allows users to authenticate and transfer digital files, or digital money without a middleman, anonymously. The innovative technology simultaneously gave birth to crypto-currencies, aka Bitcoin. And according to the history of ransomware laid out at Tech Beacon.com, given the growing advancements in and spread of infectious malware coupled with blockchain networks and the growing global acceptance of crypto-currencies like Bitcoin as a form of payment, needless to say, the welcome gates for cyber-criminals are wide open.
In the last two years cyber-attacks have dramatically increased, mostly from bad actors in Russia and China, not looking for glory or winning a war, or shutting down a pipeline, or closing a hospital or a government agency, rather it’s all about the money. According to a recent CyberCrime Magazine report ransomware is the fastest growing form of malware infecting a new online victim every few seconds, and extracting an estimated $20 billion in global ransom paid last year with US citizens and businesses paying close to $1 billion in cash.
Who is Most Vulnerable?
In May 2021, a $1.3 billion-dollar east coast oil pipeline transport company, Colonial Pipeline, was hacked! The company was locked out of its own computer systems which in turn shutdown fuel flows to major airports and storage facilities from Texas to New York creating widespread panic gasoline buying along the east coast. Colonial Pipeline said it paid $4.4 million ransom in Bitcoins for the keys to its own data. And while the FBI was able to recover some of the ransom in Bitcoin by secretly obtaining access to the thieves’ own passcode, “the attacks are going to get much worse,” says FBI Director Christopher Wray. A fortunate end for Colonial. But for JBS Foods the outcome wasn’t so lucky.
In June the CEO of meat giant JBS Foods, a $52 billion-dollar global meat processor announced that its computer systems had been hacked and held for ransom by an offshore criminal group. Despite its annual IT budget that topped $200 million, and an army of more than 800 IT staffers, the walls of Rome fell to the Vandals. This time without lifting a sword, or uttering a word the mighty JBS Foods was down, and it hurt. Their data had been co-opted and access encrypted by thugs who essentially shut down JBS meat operations in key facilities in the US, Canada and Australia. And unless JBS paid up, the hackers could put the giant out of business permanently, which begged the question to me: What would you do if your company got hacked for ransom?
“This was a very difficult decision to make for our company and for me personally,” said Andre Nogueira, CEO, JBS USA. “However, we felt this decision had to be made to prevent any potential risk for our customers.”
As reported, JBS Foods paid $11 million in ransom, meaning they got caught with their britches down despite the budget and staff. Some say they got off cheap, the damage could have cost tens of millions more.
Earlier this year the U.S. Justice Dept set up a cybersecurity task force to investigate the growing ransomware attacks and potential risks to America’s critical infrastructure, national security, and the use of cryptocurrencies in criminal activities. According to task force Deputy Director Lisa Monaco, in her June 7th DOJ news briefing the message to governments and corporations everywhere could not be more to the point:
“… the threat of severe ransomware attacks pose a clear and present danger to your organization, to your company, to your customers, to your shareholders, and to your long-term success. So, pay attention now. Invest resources now. Failure to do so could be the difference between being secure now, or a victim later.”
And she’s not overstating the size of the problem. NATO recently announced the alliance will step up efforts to combat increasing cyber threats to critical infrastructure from bad actor nations.
The trouble at home is clearly not enough smaller companies are getting the message. Despite eye-popping hair-on-fire ransomware payments making headlines these companies simply lack the sense of urgency and extra budget to secure their castle from the growing hordes of marauding cyber-hackers. And while larger corporations remain the primary targets for offshore ransomware attackers looking for bigger fish, the number of Johnny-come-lately cyber-crooks has exploded recently, targeting individual and small business computers everywhere.
According to the independent tech-review firm TechJury.net hackers are out of control:
- Globally, 30,000 websites are hacked daily.
- 64% of companies worldwide have experienced at least one form of a cyber attack.
- There were 20M breached records in March 2021.
- In 2020, ransomware cases grew by 150%.
- Around 94% of all malware is spread through email.
- Every 39 seconds, there is a new attack somewhere on the web.
- An average of around 24,000 malicious mobile apps is blocked daily on the internet.
What to Do Now…
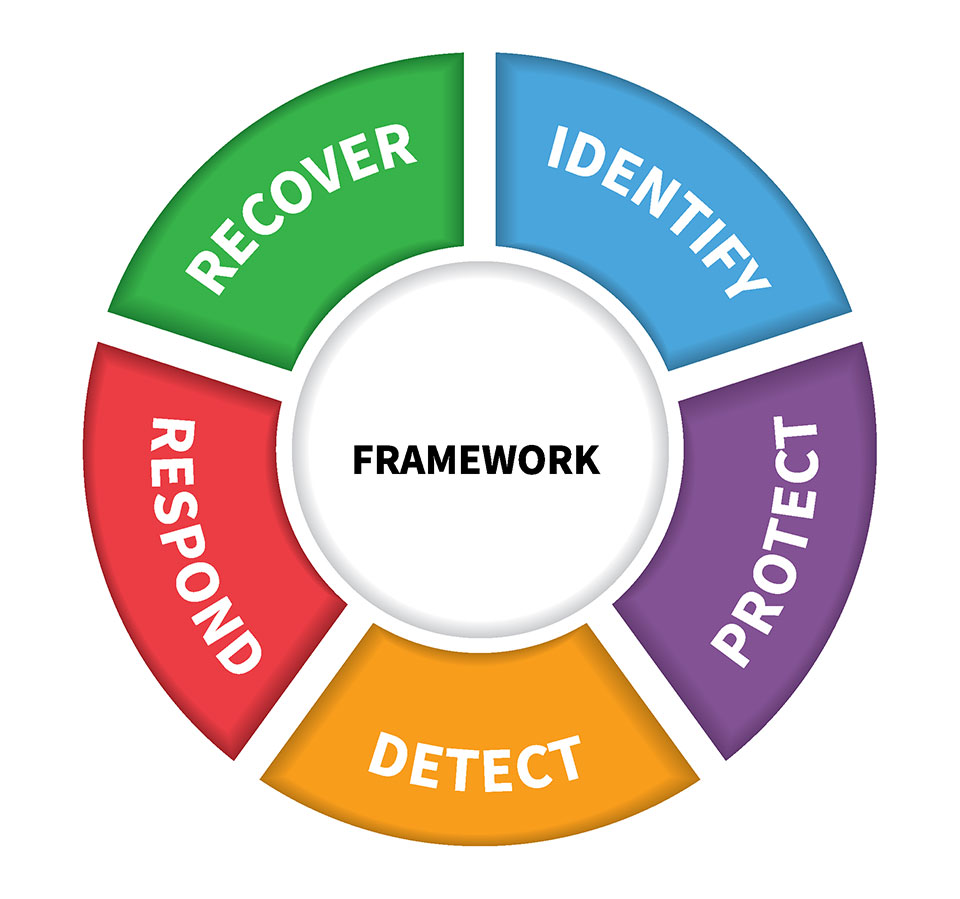
The US Dept of Commerce’s National Institute of Standards and Technology (NIST) Computer Security Resource Center has a first-step guide for business cybersecurity. They break down the approach into 5 key categories:
- Identify
- Protect
- Detect
- Respond
- Recover
I recommend you read this guide and familiarize yourself with a few simple fixes like 2-stage password authentication and limiting data access to employees that don’t need access, and training your employees on the important Dos & Don’ts and deadly dangers of random computer mouse-clicks. These are the fundamental success factors for most companies. But what about your insurance?
Cyber Security Business Insurance
No. Your general liability business insurance policy does not cover cyber-related losses. And no, you can’t buy standalone cyber liability insurance. It’s a newer insurance arena and is considered an add-on to your general liability policy coverage. But coverage is widely available, although payouts may be limited (eg: $1-5 million), or restricted to a narrow range of expenses incurred to recover from a cyber-related incident. More comprehensive policies however do include coverage for catastrophic business discontinuity and ransomware. So, it’s worth investigating.
Financial research firm Investopedia researched The 5 Best Cyber Insurance Companies of 2021 and lays out the pros and cons. Since the insurers are insuring against the financial fallouts of a major data breach, they need to know how to stay up to date on new developments and they do so in part by working closely with IT security software firms like Symantec and Norton. As a result, despite policy payout limitations it could be a good place to start. Call your business insurance agent and know that your annual insurance premium is related to your company’s implementation level of recommended cyber-risk mitigation measures. The less protected you are the higher the premiums at first. But as you increase security levels premiums drop. The US government created the Cyber & Infrastructure Security Agency for impartial advice on buying CI.
Hiring a Cyber Security Firm
There are dozens of helpful cybersecurity consulting firms for hire on Google. But if you know you’re at risk and have only a few resources to help, you may benefit most from hiring a freelance cybersecurity consultant to get things started. A single expert can conduct a quick cybersecurity system review and provide a list of immediate remedial quick-fix suggestions to patch any obvious gapping vulnerabilities, while you work on a more comprehensive solution.
Taking the Leadership Role
Clearly as hacks and attacks increase with demand for remote data access proliferating post-Covid, so doubles the focus on IT security. We are just now witnessing the growing concerns of yet another cross-border public menace. And like the Coronavirus special attention must be given to mount a global defense against these attacks and to prevent their spread and infection. But until then, we’re all on our own. And while there is an abundance of cybersecurity YouTube videos to get you started, there is no replacement for intrepid leadership and a competent IT security team to step-up and develop a tailored defense plan post-haste.
Like the FBI, the Dept of Justice, the Commerce Dept and every IT professional I know, I advise you to take action right now, before you get hacked. Get a cybersecurity expert to review your strengths and weaknesses this week, before you go on vacation, and before you find yourself up early one morning buying expensive Bitcoins to pay faceless thugs for the keys to your own shop.
Make sense?
—-
It’s 6:30am, 4 hours later at your office. You’re standing at the window in your daughter’s slippers, a new morning sun breaks the distant horizon. Your IT manager pops in. “You ok Boss? We got the ransom down to $50 million.” You look down at the parking lot far below. “I was just wondering how far to the ground it is from here?”
Written by Rick Andrade.
Bring the best of the CEOWORLD magazine's global journalism to audiences in the United States and around the world. - Add CEOWORLD magazine to your Google News feed.
Follow CEOWORLD magazine headlines on: Google News, LinkedIn, Twitter, and Facebook.
Copyright 2025 The CEOWORLD magazine. All rights reserved. This material (and any extract from it) must not be copied, redistributed or placed on any website, without CEOWORLD magazine' prior written consent. For media queries, please contact: info@ceoworld.biz








