Managing Data and Access in the Cloud

In the old days, before the advent of cloud applications and data storage, life was a bit easier on the IT staff. They could easily manage access to applications and data shares since everything was located on servers in the next room. The number of applications was usually moderate and the number of people that required access to sensitive data was nominal. For more advanced IT operations, simple scripts could be written to take user information from the directory service and automate the processes. In larger organizations, a help desk could easily manage these processes which were a huge improvement over the paper trail that had existed for years.
Once the cloud became pervasive in the corporate environment, the old methodologies of managing user and data access became significantly more complicated. Writing simple scripts was no longer an option because the applications now required complicated web services as an interface, if they provided anything at all. More often, provisioning and setting roles for a user required a time consuming manual process. In some cases an API could handle part of the provisioning but not the entirety. One extremely popular cloud application currently does provide tools to automate the user management process but, it does not automatically select what type of license to apply to the user.
—–
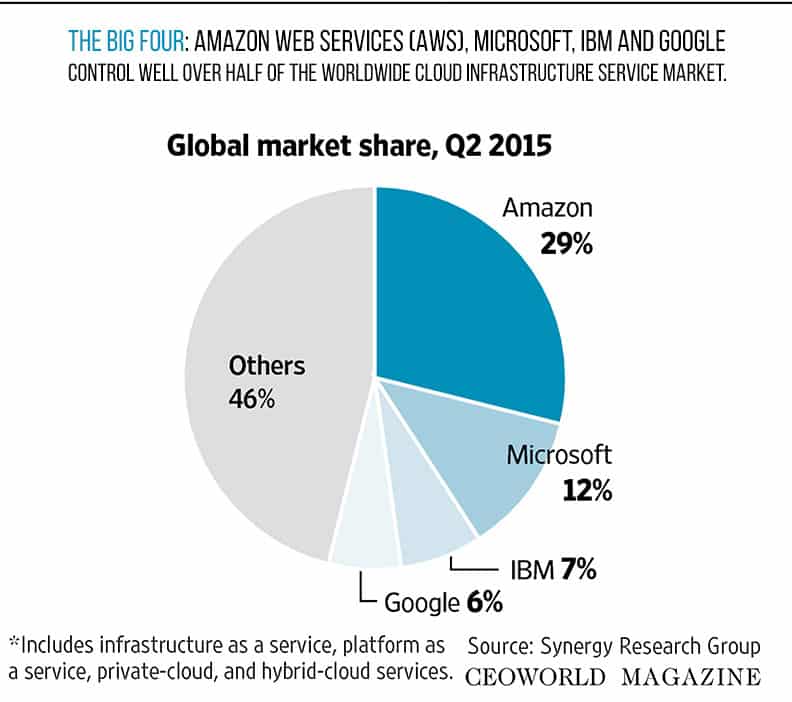
[2015 cloud computing market: The Big Four: Amazon Web Services (AWS), Microsoft, IBM and Google control well over half of the worldwide cloud infrastructure service market.]
——
So how do IT departments regain control of the cloud while reducing the amount of time and effort spent to insure users have access only to products and the data they need to perform their jobs and, at the same time, make sure access is terminated in a timely fashion? A wide variety of commercially available identity and access governance (IAG) solutions have expanded their offerings to include managing the cloud as easily as in-house systems.
Using data from an authoritative source, usually human resources, these IAG systems have the built in capabilities of communicating to an ever-increasing number of cloud-based solutions. By using the authoritative source, employment status – active or terminated – can be determined along with the employee’s title, department and location. This information can be utilized as part of a role-based access control (RBAC) matrix to determine what applications and data they should be granted rights to. In the case of a terminated status, all access would be revoked.
Using an automated system to create and delete users from the network and cloud-based systems can be a tremendous time saver. It can also increase security and governance by insuring accounts are provisioned correctly from the onset, as well as removed when no longer needed. Another area of concern however is a user getting access to an application or data for a special project, or while filling in for an employee on leave. It is critical that audits be performed on a regular basis to insure rights remain at the levels they should and there are not rogue or long-term access rights that should not be allowed.
As part of most IAM systems, a governance and attestation module comes in to play to address these situations. The network and cloud apps are scanned on a regular basis for the actual moment in time rights and these are compared against the RBAC matrix, which contains the standard or accepted rights. Where discrepancies are found, the attestation module should alert a manager and system owner for review. If the deviation is considered acceptable, an electronic signature should be contained verifying this fact and possibly an expiration date for the rights as well. If the rights are found to be unauthorized, a workflow process can automatically process the removal of the rights with notifications emails to the appropriate parties involved.
To minimize rights being added in an ad hoc fashion, a workflow management system can be utilized to administer all requested changes to the network and cloud applications. A self-service portal is established where all users are directed to make requests for new and enhanced requests. Once the end user processes the request, it is routed to the appropriate manager and systems owner for approval. The penultimate step is a review and approval by the IT department and once this step is completed, an automated process is executed to make the necessary changes across the respective systems.
To lock down rogue access even further, administrative rights to the network, on premise and cloud systems should be highly restricted and granted to a minimal number of individuals. By doing this, all changes can be forced to be completed through the workflow application which will provide detailed logs, with approvals, for any changes made to the standard.
In summary, managing the cloud applications can appear to be very daunting at first pass. However, the commercially available tools that you have been using, or are considering, can easily be extended to manage all of your on premise applications, the network, and those hosted in the cloud.
By Dean Wiech.
Bring the best of the CEOWORLD magazine's global journalism to audiences in the United States and around the world. - Add CEOWORLD magazine to your Google News feed.
Follow CEOWORLD magazine headlines on: Google News, LinkedIn, Twitter, and Facebook.
Copyright 2025 The CEOWORLD magazine. All rights reserved. This material (and any extract from it) must not be copied, redistributed or placed on any website, without CEOWORLD magazine' prior written consent. For media queries, please contact: info@ceoworld.biz








