Improving Application Management: 4 Critical Components
Applications are the new business software, fundamentally, they cover the same technology ground, but many companies are now opting for easily consumable apps over traditional software solutions. Consider the recent rise of Software as a Service (SaaS) and data from research firm Gartner suggesting that by 2017, 25 percent of enterprises will run their own “app stores,” which contain corporate-sanctioned programs for use on PCs and mobile devices.
Though the skyrocketing number of business apps raises a significant concern: oversight. Here are four ways your company can improve day-to-day application management:
Security by Design
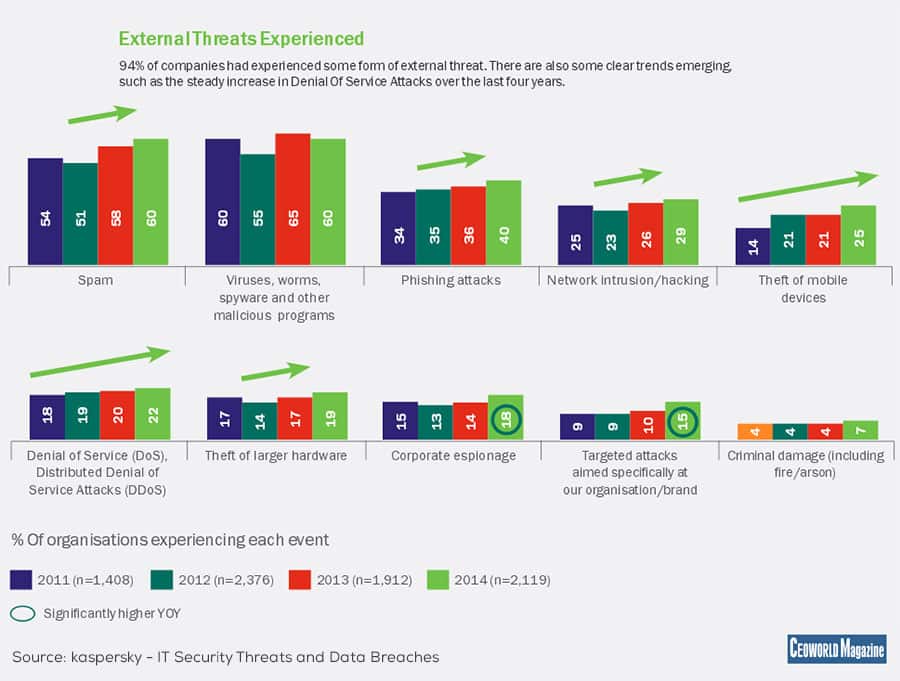
First is security. A recent article on application readiness discusses some of the challenges faced by businesses when it comes to security, such as public app stores and the need for consistent updating. While third-party app stores provide a convenient way for employees to download new productivity tools, Gartner warns that these apps may “disrupt IT security, application and procurement strategies.” Security firm Kaspersky Lab, meanwhile, found that only 52 percent of companies surveyed said that they regularly patched or updated applications, which the firm describes as “an important task in preventing malware attacks or data breaches.”
How do companies create an application management (AM) strategy that makes security the top priority? It starts before a single app is downloaded, and depends on two things: Cohesive policy and consistent automation. IT departments must devise a set of standards for all applications, regardless of device, and then apply these standards to any app request. Next, automated processes must be developed to process application requests and install procedures, making it easy for employees to download approved apps and eliminating the chance of manual errors. By investing in security by design, your company can prevent accidental, insecure downloads and limit the spread of “shadow IT” users operating outside the purview of technology professionals.
Lifecycle Considerations
Next on the list of AM techniques is getting a handle on legacy applications. As noted by About: Virtualization, the lifecycles of applications and hardware were once closely intertwined. However, as apps moved off local stacks and into colocation data centers or the cloud, the impetus for “retiring” legacy applications largely disappeared. As a result, many programs are now in use long past their prime and contribute to network inefficiencies, such as incompatibilities with other apps or lack of support from developers.
Dealing with legacy applications means setting up a regular review process whereby specific apps are examined in three key areas: function, form and foundation.
• Function describes what an application does: What specific task was it designed to accomplish, and do any other, newer, applications overlap with its mandate?
• Form speaks to the impact of an application’s code on your network: Does it cause bandwidth issues or long wait times for users or admins?
• Foundation addresses the issue of centrality: Is the app a keystone of your business model? If so, what would replacing it cost, long and short term?
In cases where apps are no longer serving unique functions, are hogging network resources and are no longer critical to business function, it’s advisable to remove them altogether and increase overall performance. Arranging regular lifecycle assessments can help keep networks clean and apps relevant.
Integration on Demand
Next on the list is app integration, specifically as it pertains to mobile devices. Unlike mobile device management (MDM), mobile application management (MAM) assist with “software delivery, software licensing, configuration, application lifecycle management (ALM) and usage tracking,” according to Tech Target. In other words, this is the mobile version of server-based AM, but running two management systems side by side only scratches the surface of improved app control. For businesses to truly get a handle on their evolving app ecosystem, it’s critical to design an AM solution that works equally well across desktops and mobile devices to provide the same ease of use, standardization and security controls. By eliminating the “gap” between mobile and workstation, it’s possible to significantly improve the efficiency of your AM.
Outsourced AM
For many companies, the prospect of developing effective security, legacy and integration controls is daunting in terms of time and cost. It’s no surprise, therefore, that hosted application management is on the rise; as noted by WhaTech, the U.S. market for outsourcing AM is headed for a CAGR of 14.09 percent over the next three years.
Beyond time to deployment and IT budget constraints, there’s another key reason for the rise of hosted application management: Flexibility. With the adoption of apps now spreading beyond traditional uses such as word processing and document sharing to include everything from analytics to HR reporting to CRM tools, it’s almost impossible for local IT to keep up with the influx; even with automated request, install and update procedures and the sheer number of apps which require management can quickly consume IT man hours. Hosted AM solutions, meanwhile, allow your company to scale up on demand to meet the needs of new users, new app segments or the push into new global markets.
Improving your application management means focusing on four key areas: security, lifecycle, integration and outsourcing to achieve the ideal combination of access, use and oversight.
Add CEOWORLD magazine to your Google News feed.
Follow CEOWORLD magazine headlines on: Google News, LinkedIn, Twitter, and Facebook.
This report/news/ranking/statistics has been prepared only for general guidance on matters of interest and does not constitute professional advice. You should not act upon the information contained in this publication without obtaining specific professional advice. No representation or warranty (express or implied) is given as to the accuracy or completeness of the information contained in this publication, and, to the extent permitted by law, CEOWORLD magazine does not accept or assume any liability, responsibility or duty of care for any consequences of you or anyone else acting, or refraining to act, in reliance on the information contained in this publication or for any decision based on it.
Copyright 2024 The CEOWORLD magazine. All rights reserved. This material (and any extract from it) must not be copied, redistributed or placed on any website, without CEOWORLD magazine' prior written consent. For media queries, please contact: info@ceoworld.biz
SUBSCRIBE NEWSLETTER








